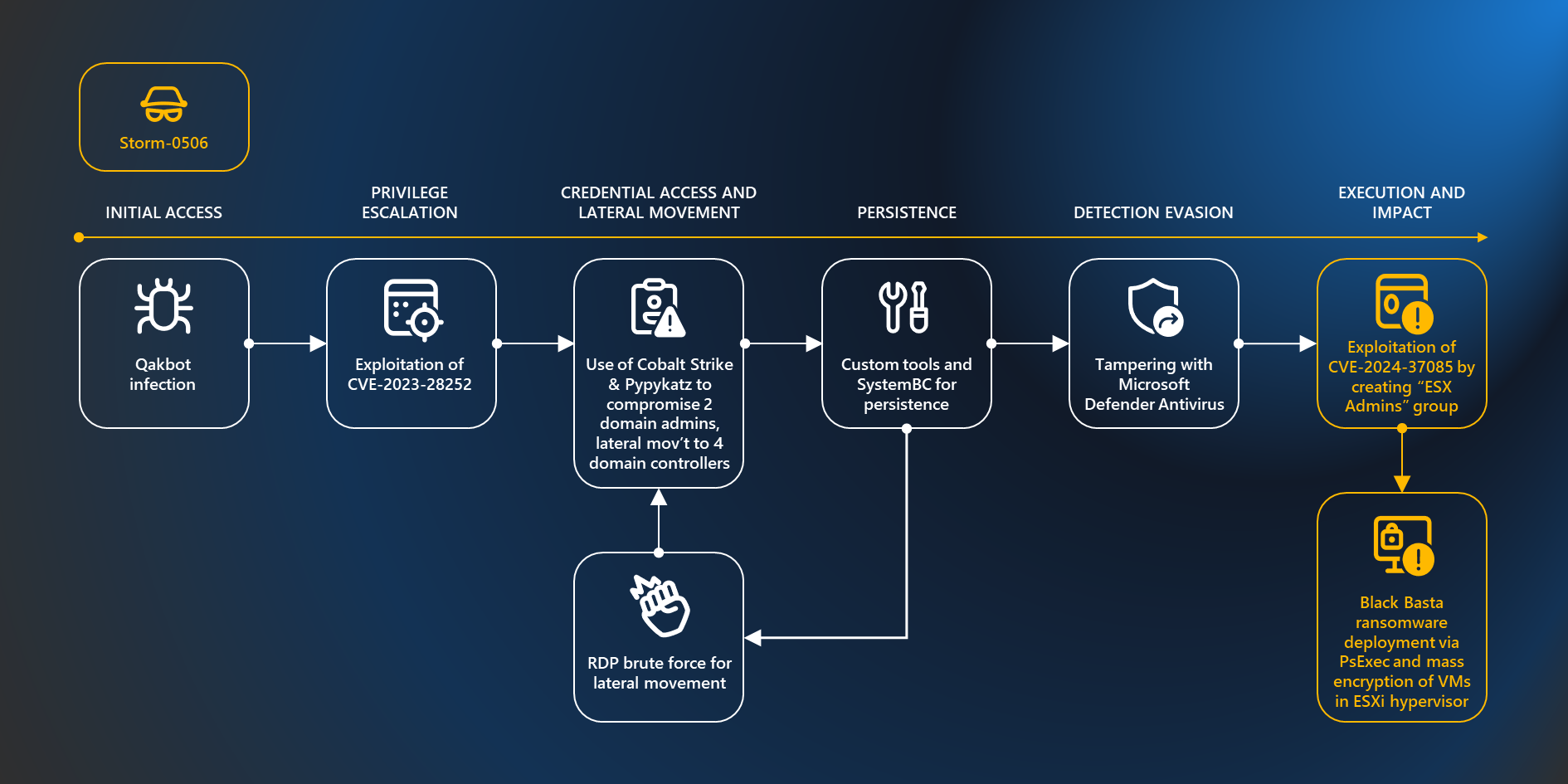
Microsoft researchers have uncovered a critical vulnerability in ESXi hypervisors, actively exploited by several ransomware operators to gain full administrative control over domain-joined servers. ESXi, a bare-metal hypervisor, is directly installed on physical servers, offering direct control of underlying resources. These servers host virtual machines (VMs), often containing critical systems within a network.
The vulnerability, labelled CVE-2024-37085, arises from a default configuration flaw. A domain group named "ESX Admins" is granted full administrative access to the ESXi hypervisor without proper validation. This group is not a standard Active Directory group and doesn't exist by default. However, ESXi hypervisors, upon joining a domain, automatically grant full administrative rights to any members of a group with this name, regardless of its original existence.
This vulnerability has been actively exploited by ransomware operators like Storm-0506, Storm-1175, Octo Tempest, and Manatee Tempest, often leading to Akira and Black Basta ransomware deployments. These attackers exploit the vulnerability by creating the "ESX Admins" group in the domain and adding their own user accounts to it, gaining full control over the ESXi hypervisor.
How the Vulnerability Works:
Three methods of exploitation have been identified:
1. Group Creation & User Addition: The most commonly used method involves creating the "ESX Admins" group and adding a user to it. Any user with the authority to create groups can exploit this vulnerability.
2. Group Renaming & User Addition: This method involves renaming an existing group to "ESX Admins" and adding a user or utilising a pre-existing group member.
3. ESXi Hypervisor Privileges Refresh: Even when a network administrator assigns a different group as the management group for the ESXi hypervisor, members of the "ESX Admins" group retain full administrative privileges until they are explicitly removed. This method has not been observed in the wild.
Ransomware Operators Targeting ESXi Hypervisors:
Over the past year, there has been a significant increase in ransomware attacks targeting ESXi hypervisors. This trend is driven by the ease of mass encryption and the potential to stay undetected by security systems.
Reasons for Targeting ESXi:
Limited security product visibility and protection for ESXi hypervisors.
Encrypting the ESXi file system offers one-click mass encryption of hosted VMs, giving attackers more time to move laterally and steal credentials.
This vulnerability poses a significant risk to organisations using domain-joined ESXi hypervisors. Successfully exploiting the vulnerability grants attackers complete control over the hypervisor, allowing them to:
Encrypt the file system, potentially rendering hosted servers unusable.
Access hosted VMs, potentially exfiltrating data or moving laterally within the network.
Mitigation and Protection Guidance:
Microsoft strongly recommends that organisations using domain-joined ESXi hypervisors:
Install software updates: Immediately apply the security update released by VMware to address CVE-2024-37085. If immediate updates are not possible, consider:
Validating and hardening the "ESX Admins" group, if it exists.
Changing the ESXi hypervisor's admin group to a different group.
Implementing custom detections in XDR/SIEM for the new group name.
Configuring ESXi logs to a SIEM system to monitor suspicious administrative access.
Credential hygiene:
Implement Multi-Factor Authentication (MFA) for all accounts, removing any exceptions.
Enable passwordless authentication methods for supported accounts.
Isolate privileged accounts from productivity accounts to enhance security.
Improve critical asset posture: Identify and protect critical assets like ESXi hypervisors and vCenters with the latest security updates, monitoring procedures, and robust backup/recovery plans.
Identify vulnerable assets: Use authenticated scans of network devices via the Microsoft Defender portal to identify vulnerabilities and receive security recommendations.
Detection and Response:
Microsoft Defender for Endpoint and Microsoft Defender for Identity can assist in detecting suspicious activity related to this vulnerability. Alerts regarding modifications to the "ESX Admins" group, new group creation, and suspicious account manipulation should be investigated promptly.
Microsoft Defender XDR and Sentinel:
Microsoft Defender XDR customers can use hunting queries to identify ESXi hypervisors and track changes to the "ESX Admins" group. Microsoft Sentinel users can leverage TI Mapping analytics to automatically detect malicious activity associated with this vulnerability.
Conclusion:
The exploitation of CVE-2024-37085 highlights the critical need for organisations to proactively address security vulnerabilities in their IT infrastructure. By following the mitigation and protection guidance outlined above, organisations can significantly reduce their risk of falling victim to ransomware attacks targeting ESXi hypervisors.